Brought to you by
Is ‘Problem in Chair, Not in Computer’ a cyber security misnomer?
No PICNIC
Malware and other malicious security breaches often enter an organisation through the actions of the individuals who work there – whether it’s simply falling for a phishing email or there’s more elaborate social engineering at play.
This digital content experience will share bespoke research findings into how IT leaders perceive the role of endpoint hardware, and remote manageability, in modern cyber security strategy.
Challenging landscape

65
of those polled are experiencing up to ten cyber security incidents every week
%
78
expect the cyber security landscape to become harder to navigate over the next few years
%
On average, organisations ranked their confidence in endpoint security at around 7/10
When asked to rate the effectiveness of this training, those participating rated in at around 7/10
The below-the-OS cyber security capabilities of endpoint devices are a priority for only 1-in-4 of those surveyed when specifying endpoint devices
Phishing and malware were considered the greatest threats to cyber security
61
conduct employee security awareness training between once and three times a year
%
Key Findings
As 2021 draws to a close, the cyber security landscape isn’t a pretty sight. Firstly, attack volumes have increased as more technically advanced cyber crime groups seek to expand their professional networks by recruiting less advanced groups. The National Cyber Security Centre (NCSC) said recently that it had recorded a 7.5 per cent increase in cyber incidents in the year to August, with ransomware attacks accounting for a majority of the damage. GCHQ said last month that it had seen a doubling of ransomware attacks on UK institutions in the last year.
Secondly the nature of attacks has changed with many targeting closer to ‘the metal’, shifting from OSs, browsers, and applications to firmware and BIOS levels. Attacks are configured to move laterally through networks, seeking out backed up copies of data to give attackers maximum leverage. There has also been a pivot to using data exfiltration alongside encryption which further reduces the ability of the victim to fight back by publishing or selling off some or all stolen data. If victims refuse to engage, attackers can publicise the attack should they choose to do so.
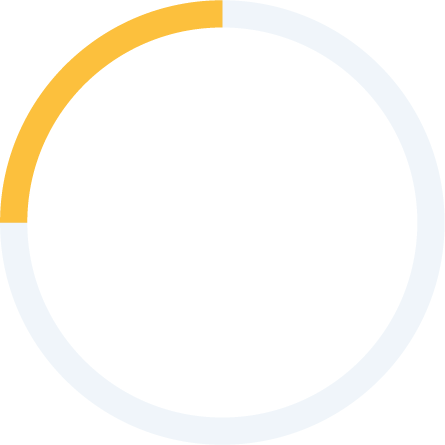
Most think that the cyber security landscape is likely to become darker in the next two years. 64 per cent expect the number of cyber security incidents at their organisation to increase somewhat over this timescale and a further 14 per cent expect it to increase greatly. 21 per cent expect things to stay much the same.
How many of our research participants had experienced a cyber attack landing at their organisation? This can be a tricky question to ask because organisations tend not to be forthcoming about having experienced security breaches. Nonetheless, 30 per cent said that they had experienced a successful attack and a further 11 per cent weren’t sure. This compares with a much higher reported global average of “ransomware victimisation” of 62 per cent in 2020 and almost 69 per cent so far this year.
recently recorded an increase in cyber incidents in the year to August, with ransomware attacks accounting for a majority of the damage

When we ask enterprises what they consider their greatest security challenges to be two answers dominate the table – phishing and malware/ransomware. Of course, the two are linked, with phishing emails being the transmission mechanism for the majority of malware. Whether ransomware is delivered directly or indirectly, email remains the vector of choice for the majority of attacks.
People problems
Phishing is so widely used because it works, and it all comes back to the employees themselves. Phishing weaponises our humanity – our desire to do a job well, our kindnesses, curiosities, concerns and fears. The second tranche of cyber security threats listed above very much relates to people – a lack of awareness of cyber security matters, end user mistakes and browsing habits and remote working vulnerabilities.
Employees are more vulnerable to phishing if they are working in solitude. In an office environment it’s easier to run something past a colleague and being in a corporate environment probably results in a slightly more guarded mindset. At home, this isn’t the case, and domestic distractions might well make it more likely that a phishing attempt which might have been picked up in the office, gets missed.
People who work in technology, particularly in tech support functions can become frustrated with the employees they support. Employees are sometimes accused of a lack of awareness on the importance of cyber security or sometimes a more general lack of awareness about technology. The acronym PICNIC (Problem in Chair, Not in Computer) is an example of this, as is the slightly more niche “layer 8 issue.” It’s very easy to see how stressed-out support professionals might occasionally respond with flippancy.
However, employees who, by definition, are unlikely to have the same understanding of the risks that their use of technology can pose for both them and their employers that technical teams have, are likely to respond better to education and support rather than they do to being made to feel like a liability.
7.5
%
The cyber security landscape is getting harder to navigate for cyber security professionals who are charged with trying to protect their organisations from data compromise and loss. Phishing and malware are considered the most significant cyber security threats that organisations face, with poor employee awareness, poor web hygiene and remote working vulnerabilities among the next most widely cited fears. Yet, the professionals we spoke to rate their confidence in endpoint security slightly higher now than they would have done pre-pandemic.
Whatever they have confidence in, it generally isn’t employees. The majority of those who took part try to reach employees with security awareness training between once and three times a year but only rate that training effectiveness at reducing cyber security incidents at slightly less than 70 per cent. Barely more than a quarter said they were completely happy with employee security awareness training at their organisation.
Conclusion
Below-the-OS security helps prevent endpoint compromise
Most enterprises, aware that the vulnerability of some of their end users and the increasing sophistication and ruthlessness of the cyber-criminal underworld is a highly flammable mix, try to blend technology and training to reduce the chances of compromise and mitigate the risks that their organisations face. 83 per cent of those taking part in our research agreed either somewhat or strongly that “the most effective user device security strategies combine software, hardware, and cyber risk training.”
Every organisation has some sort of endpoint protection software in place, although it will vary between more traditional AV and anti-malware type products through to EDR and UES, combined with IAM. When we asked participants to rate the importance of below-the-OS (hardware/firmware-level) endpoint security in preventing and limiting cyber security incidents at their organisations the average rating was seven out of a possible ten.
That would suggest that the security properties of endpoints themselves are not the first consideration of those making endpoint buying decisions, and the responses to the question shown below further emphasise this point, although it’s notable that only 17.4 per cent of those responding rely solely on third party security software.
The Importance of Capable Hardware
These findings suggest that employees need more help to remain secure and productive, and security support teams need technology solutions which enable them to properly support employees. Part of the Intel vPro® platform, Intel® Active Management Technology (Intel® AMT) and Intel® Endpoint Management (Intel® EMA), allow support teams to remotely manage and support laptops, regardless of their state or location. This means that security patches can be pushed out even if an employee leaves a device powered down and asset data can be collected.
Sponsor Insight
The big question
GCHQ
said last month that it had seen a doubling of ransomware attacks on UK institutions in the last year

expect the number of cyber security incidents at their organisation to increase in the next two years
64
%
The landscape ahead for cyber security
Find out more
For 38 per cent of the organisations represented, between one quarter and all of the cyber security incidents that had affected them had originated from a compromised user device. This is happening because ransomware and other types of malware are evading software-only based detection, compromising endpoints, stealing encryption keys and credentials, and accessing networks, cloud and SaaS applications – completely bypassing perimeter-based network security.

are completely happy with employee security awareness training at their organisation
1 in 4

Introduction | Key findings | Challenging landscape | People problems | The importance of capable hardware | Conclusion | Sponsor info
The illustration below shows just how rarely employees get to choose the device
Never
3%
11%
Less than once a year
39%
Once a year
9%
Only when they join the organisation
Greatest cyber security challenges faced (3 maximum)

Intel (NASDAQ: INTC), a leader in the semiconductor industry, is shaping the data-centric future with computing and communications technology that is the foundation of the world’s innovations. The company’s engineering expertise is helping address the world’s greatest challenges as well as helping secure, power and connect billions of devices and the infrastructure of the smart, connected world – from the cloud to the network to the edge and everything in between.
Visit the newsroom
Visit the newsroom
Visit the website
Visit the website
About the sponsor
Find out more about Intel
Developed for the IT professionals of today and tomorrow, the Intel vPro platform is built for business. With each component and technology designed for professional grade, IT can be confident with tools to enhance everyone’s productivity, help secure their business’ data, remotely manage critical devices, and build their fleet on a reliable platform.
The research examines how capable hardware, with baked in enterprise-level security features and management capabilities, can help to overcome cyber risks posed by employees – and those who target them.
Read on to learn more about these findings and what they mean for your organisation



Many businesses rightly invest in regular cyber risk training to ensure employees are aware of the threats they face and how to avoid them.
Despite the best intentions and even with regular training on cyber security risks, accidents can happen. We’re all human and humans make mistakes. This is why, to protect both employer and employee, ensuring you have technology in place can help minimise the impacts of human oversight, or even exposure to the risks in the first place.
The acronym PICNIC (Problem in Chair, Not in Computer) is a somewhat flippant term used in IT troubleshooting, but it perpetuates a false dichotomy that exists in enterprise IT – that the human and technology challenges organisations face are somehow distinct.
The reality is that technology can both solve and create problems. It can be a productivity driver or a frustrating point of friction, a defence against attack or a cyber security vulnerability.

Other highlights

We can see here the volume of attacks that those participating in this research are having to fend off.



If you can prevent breaches at this low level, it goes a long way to preventing OS breaches, the CPU chip has to be secure to protect the BIOS & kernel
Below the OS capabilities prevent user tampering, ensuring security is as deployed, and helps discourage opportunistic theft
They help us protect against and prevent cyber-attacks and play an important role in our system
That “below-the-OS” security capabilities of endpoints can be an afterthought for some of the organisations represented was also visible in the fact that only 66 per cent agreed that “below-the-OS endpoint security is essential to a capable cyber security strategy today.” Whilst 66 per cent constitutes a majority it can hardly be said to demonstrate universal agreement. A similar proportion – 68 per cent - agreed to at least some extent that “my organisation recognises that the endpoint devices you buy make a difference to your cyber risk profile.”
The numbers above provide a clue that responses to a question about the role that capable hardware plays in cyber security strategies, were mixed.




Part of the Intel vPro® platform, Intel® Hardware Shield provides enhanced protections against attacks below the OS and advanced threat detection capabilities for increased platform security. It adds a deep layer of security to further protect enterprise data and enhance the efforts and impact of cyber security professionals without disempowering employees.
Sponsor Insight
Find out more
By being able to use AI-powered threat detection to identify malware, such as ransomware or crypto mining running on a system, and using CPU telemetry to effectively signal to EDR software that there is a problem with that particular endpoint, hardware level cyber security can optimise the performance of EDR software. Because all of this is happening at a hardware level, there is no negative impact on the performance of the endpoint.
Those seeking to breach enterprises with ransomware, or other types of compromise, so ruthlessly target humans, any defences have to work with employees, not disempower them. While hardware and firmware-level security is not a standalone solution, it is a firm foundation upon which to build a broader cyber security strategy also consisting of EDR software and risk awareness training.
The devices that remote workers use greatly affect cyber risk profile, and cyber security stance should be a key part of the process when endpoint purchasing decisions are made.
Given the concern about employee awareness and the nature of many threats which are bypassing software-based security measures, it is reasonable to assume that the cyber security of the hardware itself, at a “below-the-OS” level is considered when making purchasing decisions. However, the security characteristics of hardware are not being given, in many cases, the consideration that they should be, despite two-thirds also agreeing that endpoint devices affect risk profile.
This confusion about the role of “below-the-OS” security capabilities is leading to compromise. For 38 per cent of the organisations represented, between one quarter and all of the cyber security incidents that had affected them had originated from a compromised user device.
Below-the-OS security features can play a vital role in strengthening cyber security stance. In particular, attacks that target memory can be blocked, giving detect and remediate software more time to find planted malware and avoiding compromise in the meantime. Virtualisation based security can be reinforced, supporting a secure boot and ensuring endpoints run in a trusted state. Hardware based encryption adds yet another later of data protection.

Find out more








Find out more
Find out more about Intel


Introduction
Key findings
I'll tell you what I want
Different priorities
Power of personas
A bigger picture
Conclusion
Sponsor info

16
manage to retrain employees four times a year or more
%
26
said that they were completely happy with employee security awareness training at their organisation
%



38
of the organisations represented, told us that between one quarter and all of the cyber security incidents that had affected them had originated from a compromised user device
%

Number of genuine cyber security incidents per week
None
13%
1 - 5
53%
6 - 10
12%
11 - 20
11%
21 - 50
5%
51 - 100
3%
More than 100
3%
1
2
3
30
%
said that they had experienced a successful attack
We asked those participating to rate their confidence in endpoint security break this down into pre and post pandemic assessments.
Average score = 6.99
Average score = 7.14
1
2
3
4
5
6
7
8
9
10
1%
1%
3%
2%
8%
18%
28%
27%
9%
4%
0%
0%
1%
4%
8%
19%
24%
28%
11%
5%
Confidence in their endpoint security before the pandemic
Confidence in their endpoint security since the pandemic?
From these findings you might conclude that optimism was in short supply in cyber security circles. But that wouldn’t be entirely correct.
On a scale of 1 to 10, ‘1’ being the ‘least confident' and ‘10’ being the ‘most confident’
The last 20 months of research has shown organisations to have consistently reported a deteriorating security stance since Covid-19 appeared, with concerns about newly minted remote workers and their impact on enterprise cyber security featuring heavily.
However, this survey showed a tiny increase in endpoint security confidence from an average score of 6.99 to 7.14. Does this represent a turning of the tide on the cyber security challenges imposed by increased remote working? Or is it representative of the fact that despite the enormous changes in how we work over the last 20 months, cyber security infrastructure remains relatively unchanged?
59
%
Phishing

Malware/
Ransomware
55
%
Lack of cyber security awareness and training among employees
23
%
End-user error/web browsing habits
23
%



Remote working vulnerabilities
21
%
Poor password habits
19
%
Shadow IT
17
%
Denial of
service attacks
16
%
BYOD vulnerabilities
15
%
Lack of cyber security expertise
in the IT department
13
%
Malicious
internal activity
10
%
Inadequate
cyber security infrastructure/tools
7
%








Of course, security teams know that training is important, and the chances are that the majority would like to dedicate more time to it, but the fact that teams are understaffed, managing a continual flow of alerts and incidents, and doing so via about ten distinct products and interfaces means that time to educate others is limited. When asked about the extent of their happiness with various aspects of security strategy it is notable that only 26 per cent said that they were completely happy with employee security awareness training at their organisation.
Employee awareness training is part of this, and the vast majority of organisations do undertake this, although as the chart below shows, the frequency varies enormously. The majority try to reach employees between once and three times a year. This sounds reasonable, but the findings don’t tell us whether this is in person training with the chance to engage and ask questions or whether it’s a fixed question quiz where the content never changes, and you have to just hit a minimum pass rate to tick it off your “to do” list. This variability in training material is likely to be reflected in the average score being awarded for the effectiveness of training at reducing cyber security incidents coming in at a slightly lacklustre 6.9.
Frequency of employee security awareness training
22%
Two-to-three times a year
11%
Four-to-six times a year
5%
More than six times a year

On a scale of 1 to 10, ‘1’ being ‘not at all successful' and ‘10’ being ‘extremely successful’
Training success rate in reducing cyber security incidents
Average score = 6.9
1 2 3 4 5 6 7 8 9 10
1% 0% 4% 3% 11% 13% 29% 22% 11% 5%
Importance of endpoint below-the-OS cyber security capabilities
25
It’s a priority
%
It’s a secondary consideration
45
%
29
%
We feel most devices are similar in this respect
17
%
We rely solely on third-party software-based security, with no consideration
for the security of the hardware itself
For some, it was important:
For others, less so:
It is desirable but not essential
They have a limited role, mostly around encryption
It's not actually something that is considered



The lack of emphasis given by some organisations to endpoint hardware itself looks troubling in the light of the finding illustrated below.
Proportion of cyber security incidents originating from a compromised user device
None
1 - 25%
26 - 50%
51 - 75%
76 - 99%
All
17%
44%
17%
13%
6%
1%



2
1
1 theguardian.com
2 theguardian.com
3 .statista.com



65
of those polled are experiencing up to ten cyber security incidents every week
%
expect the cyber security landscape to become harder to navigate over the next few years
78
%
61
conduct employee security awareness training between once and three times a year
%




1
2
2
64
%
expect the number of cyber security incidents at their organisation to increase in the next two years
From these findings you might conclude that optimism was in short supply in cyber security circles. But that wouldn’t be entirely correct.
Most think that the cyber security landscape is likely to become darker in the next two years. 64 per cent expect the number of cyber security incidents at their organisation to increase somewhat over this timescale and a further 14 per cent expect it to increase greatly. 21 per cent expect things to stay much the same.
How many of our research participants had experienced a cyber attack landing at their organisation? This can be a tricky question to ask because organisations tend not to be forthcoming about having experienced security breaches. Nonetheless, 30 per cent said that they had experienced a successful attack and a further 11 per cent weren’t sure. This compares with a much higher reported global average of “ransomware victimisation” of 62 per cent in 2020 and almost 69 per cent so far this year.






Phishing
59
%

Malware/
Ransomware
%
55

Remote working vulnerabilities
21
%

Poor password habits
19
%

BYOD vulnerabilities
%
15

Lack of cyber security expertise
in the IT department
%
13



Employee awareness training is part of this, and the vast majority of organisations do undertake this, although as the chart below shows, the frequency varies enormously. The majority try to reach employees between once and three times a year. This sounds reasonable, but the findings don’t tell us whether this is in person training with the chance to engage and ask questions or whether it’s a fixed question quiz where the content never changes, and you have to just hit a minimum pass rate to tick it off your “to do” list. This variability in training material is likely to be reflected in the average score being awarded for the effectiveness of training at reducing cyber security incidents coming in at a slightly lacklustre 6.9.
1
2
3
4
5
6
7
8
9
10




If you can prevent breaches at this low level, it goes a long way to preventing OS breaches, the CPU chip has to be secure to protect the BIOS & kernel
They help us protect against and prevent cyber-attacks and play an important role in our system
Below the OS capabilities prevent user tampering, ensuring security is as deployed, and helps discourage opportunistic theft






Find out more
Find out more



RETURN TO HUB

RETURN TO HUB
